Best Practices for Transit Cybersecurity: APTA’s Operational Technology – Cybersecurity Maturity Framework
The security and stability of the nation’s public transportation systems are an important part of maintaining our way of life. As enterprise cyber-assurance projects proceed within U.S. transit, the hacking community chips away at protection strategies and any layer of protection that may have previously been effective. Maintaining safety systems and digital control of transit assets is critical to maintaining public confidence and ensuring systems function as intended. Transit agencies must take a holistic approach to cyber protection to stay ahead of a digital disaster that is always waiting around the next corner.
The National Institute of Standards and Technology (NIST) is a U.S. government agency that works with industries to develop best practices. NIST has established well-known and accepted standards produced by many experts. The security goals for Information Technology (IT) and Operations Technology (OT) have been honed by organizations like NIST for several years.
The American Public Transportation Association (APTA) uses NIST standards to better define the critical actions transit agencies should take to secure transportation networks. Implementing NIST practices is a core component of a successful security program in the hacking “arms race.” Most people are familiar with basic IT requirements because routers and Wi-Fi are a part of our daily lives, but transit agencies must secure their OT or industrial control systems (ICS) with a lesser-known set of system requirements to meet safety and security goals across all ICS systems.
APTA uses NIST best practices to help transit agencies build OT protection programs. The focus is on “maturing” an organization’s cyber preparedness. The concept is not very different from my expectation for my daughter as she soon graduates college. We have discussions about preparedness and have found there are many things she has learned in the past four years:
- There are things that she knows she knows
- There are things that she knows she doesn’t know
- There are deep things she doesn’t know she knows
- There are things she doesn’t know that she doesn’t know
Like cybersecurity in transit agencies, we celebrate the first, I try to help her with the second, we talk about the third, and the simple awareness of the last is a win as she works to discover the unknowns.
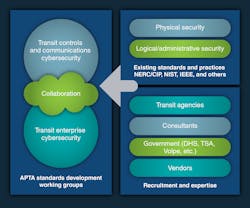
In much the same way that my daughter faces an ever-more-challenging world, APTA is concerned with the need for better cybersecurity preparedness in its member transit agencies, large and small. To help alleviate the problem, one of APTA’s many standards working groups, the Control and Communications Security Working Group (CCSWG), has been writing recommended practices and white papers for the industry for the past 14 years. The CCSWG differentiates Control and Communications Operational Technology from IT Enterprise Technology. Cyberattacks can cause great harm in ICS areas.
Most recently, in response to requests from APTA’s membership, the Transportation Security Administration (TSA) and others, the working group has developed an Operational Technology – Cybersecurity Maturity Framework (OT-CMF) overview for launching and maturing an OT program. This framework enables and empowers transit agencies to plan, implement, measure, monitor, and mature their OT cybersecurity program, so they can respond to the evolving cyber threats undermining critical service delivery and safety. Transit agencies will be able to implement the maturity framework to use what “they know they know” to work toward understanding the threats presented from the unknown and always with the goal of maturing and reaching a high state of prepared resilience.
The OT-CMF draws from existing NIST standards like NIST 800-53 (Security and Privacy Controls for Information Systems and Organizations), and its overlay, NIST 800-82 (Guide to Industrial Control Systems (ICS) Security), as well as NERC-CIP (National Electrical Reliability Council – Critical Infrastructure Protection) and various IEEE standards.
At this point, there is a need to differentiate the term requirements from controls. Whereas requirements are obligatory, controls are selected according to the organization. NIST 800-53 describes controls as:
“Controls can be viewed as descriptions of the safeguards and protection capabilities appropriate for achieving the particular security and privacy objectives of the organization and reflecting the protection needs of organizational stakeholders. Controls are selected and implemented by the organization in order to satisfy the system requirements.”
The CCSWG distilled the 965 controls in NIST 800-53 and 800-82 into 134 controls for the Cybersecurity Maturity Framework. Each control is numbered according to its topic. An example is provided in Figure 3.
Each agency is different in size, talent and financial resourcing, so the OT-CMF attempts to help organizations move past the “one-size-fits-all” approach to security. Within these controls lies the recipe for maturing individual transit agencies.
With careful, thoughtful work to build an agency-specific OT cybersecurity program, transit agencies can move their organizations up through the maturity levels. The goal is better identification of incidents, detection of anomalies, protection of systems, faster response and an organized approach to recovery.
Transit agencies that implement the OT-CMF will realize alignment with these goals with the following five objectives:
- Establish a common cybersecurity language to enable communication between the leadership and stakeholders.
- Create a consistent approach for maturing control systems’ cybersecurity programs.
- Develop a common understanding of control systems’ cybersecurity best practices.
- Enable organizations to develop data-driven risk prioritization.
- Define a path to optimize cybersecurity investments and increase cyber resilience.
The CCSWG looked to industry standards and found that five levels of maturity existed. The OT-CMF isn’t just a tool for large transit agencies. It was designed with the perspective that all organizations must start to develop a cyber-maturity program from where they are now, so a “0” level of maturity was created to credit organizations for what they are currently doing to meet security requirements. The CCSWG calls it the on-ramp. A description of the six maturity levels follows:
- Level 0 Baseline (On-Ramp) – Establish a foundation and implement minimum OT-CMF recommended controls.
- Level 1 Initiate – OT-CMF recommended controls are adopted without formal processes or documentation.
- Level 2 Planned – Establish security roles and responsibilities and a risk management program with documented policies, procedures, and processes with Key Risk Indicators (KRI) and Key Performance Indicators (KPI) aligned with the OT-CMF.
- Level 3 Operational - All OT-CMF recommended controls have been documented, implemented, and assessed at least annually. An improvement plan is reviewed and updated annually to enhance the efficiency and effectiveness of controls.
- Level 4 Managed – Continuous monitoring and improvement have been put in place to manage the controls using automated tools and technologies that respond and adapt to the changing threat landscape.
- Level 5 Optimized – Full automation of monitoring and response using technological advances (A.I.) that continuously increases efficiency, performance, and real-time reporting.
At this point, the reader may ask, “How many agencies are at a Level 5 or even Level 4?” And the answer is probably none. Those are levels to strive for and can be reached with a focused effort.
The OT-CMF overview will provide guidance on:
- Must-have cybersecurity operations technology controls
- Should-have cybersecurity operations technology controls
- Implementing operations technology controls
- Measuring the success of operations technology controls
- Achieving higher operations technology controls maturity levels
Conclusion
The safety and security of transit environments are critical to maintaining commerce, and, just as important, confidence in public transit systems. The growth of digital systems has created opportunities to do things faster and more efficiently, but this increasing digitalization comes with added vulnerabilities. Leadership within agencies must have a better understanding of how to prioritize cyber-preparedness strategies across their organization. They need a harness that can be tightened and loosened based on data-driven requirements.
Just as agencies have developed a culture of safety, new approaches to managing the IT and OT environments will need to be integrated into the culture of the transit agency to ensure smart growth, and just as the sector has created consistency through the development and adoption of standards across all transit agencies, approaches must be implemented to provide a feedback loop for sharing lessons learned. The OT-CMF tool is a key tool in achieving these goals.
-----------------
John B. Moore is the senior business development manager of U.S. Rail Infrastructure at Phoenix Contact USA.
Michael Echols is the APTA Facilitator for the CCSWG and CEO of Max CyberSecurity, LLC, located in Washington, D.C.
About the Author

John B Moore
Senior Business Development Manager - U.S. Rail Infrastructure

Michael Echols
CEO, Max CyberSecurity, LLC
Michael Echols is the APTA Facilitator for the CCSWG. He has many years of national and international experience in cybersecurity and is currently the CEO of Max CyberSecurity, LLC, located in Washington, DC.